
My New Tiny Hardware Firewall
Introduction
I’m writing a very long article on Firewalls because we just replaced our home Firewall and I was researching my options before selecting one. I was surprised to see how many new categories of Firewalls there are now. Many for home use and even some for travel…which is the category that Tiny Hardware Firewall falls into. Or, perhaps portable is a better term.
I’ve known for several years that using public networks was dangerous…but I never completely understood the extent of the danger. Nor did I know of an alternative if I had to use one.
Which is why I’m writing this post. I learned about a great solution for when you need to use public networks.
If You Don’t Want to Read Everything Just Scroll Down to Watch the Video I Label ‘Must See‘ Towards the Bottom and Read the Article Immediately Following it.
What’s a Public Network?
A public network is any network that is available for use without a password…meaning it’s unsecured and anyone can join it. So Starbucks, the airport, a business convention you might be at…any network that lets lots of strangers join it might be a better definition.
What I didn’t realize was that other public networks which may require passwords like at a hotel, hospital or a large clinic’s like Mayo in Rochester, and even onboard an airplane, may be equally dangerous. Because just a password only isn’t the thing that protects you…or the determining factor really. It’s whether or not the network is encrypted. And if it has a password there’s a better chance it’s encrypted. But non-password networks can also be encrypted…so it gets confusing. I think the safest way to think about a public network is that it’s any network that allows a lot of strangers onto it. Because for sure, it’s all those strangers that raise the risk factors a lot.
Although I didn’t understand how, I’d always assumed that when you entered a password to join a network that somehow made the network safe to use. But I was wrong…and the fact that my Facebook account has been hacked multiple times while on vacation and while using hotel networks with passwords should have been my clue.
I also learned that oftentimes using apps is even worse. Because so many apps don’t bother using secured communications. Pinterest and EBay are 2 good examples of completely unsecured apps. Last I learned that you can get into trouble even if you don’t use a public WiFi…just by leaving the WiFi receiver on your device turned on. You can learn more about that in this Time Magazine article. So if you’re using an ios device you can either turn WiFi off completely when you’re out. Or, turning on ‘Ask to Join Networks‘ if you need to leave WiFi on is better than nothing.
Why are Public Networks Dangerous?
Once again I don’t understand the exact logistics of how hacker’s do the things they do on public networks…but I do understand some of the risks…although it’s quite possible that I’m not aware of them all.
These are the main risks I know about:
- Your account credentials can be seen as you enter them and therefore stolen…which is how my Facebook account was hacked twice.
- Your personal information can be taken as well. Whether or not that occurs as a result of your actually typing it in or entering it while visiting a website…I’m not sure. But regardless this is a worrisome enough aspect for me to think twice about using a public network.
- Your web browsing activities can be watched.
The risks are probably greater than just those above…but I can only speak to things I know for a fact to be true. If you’re interested in seeing just how easy it is to hack someone’s device you can watch this YouTube video which demonstrates the 10 best Android hacking apps for 2017.
How to Protect Yourself on Public Networks
The obvious answer is to not use them. But that’s not practical for things like vacations when you need to rely upon hotel networks. Because generally your only alternative is your cell plan’s network which isn’t intended for high volume things like uploading lots of vacation photos, and can therefore become very expensive quickly.
You can take a hotspot with a better cell plan along with you and we do that too. We bought a Verizon hotspot and it’s great…but it’s expensive too. We have a small $50 per month plan because it’s monthly and many months we don’t use it. We could increase it for vacations…but we run the risk of forgetting to decrease it when we get back home…so even this isn’t a great solution. We also tried 2 different ones that we just paid for when we used them…but they had huge problems. The monthly plan options just seem to work a lot better.
I recently discovered a much better solution which is the 2nd main subject of this post…using a portable Firewall which also includes a VPN. That’s exactly what the Tiny Hardware Firewall is.
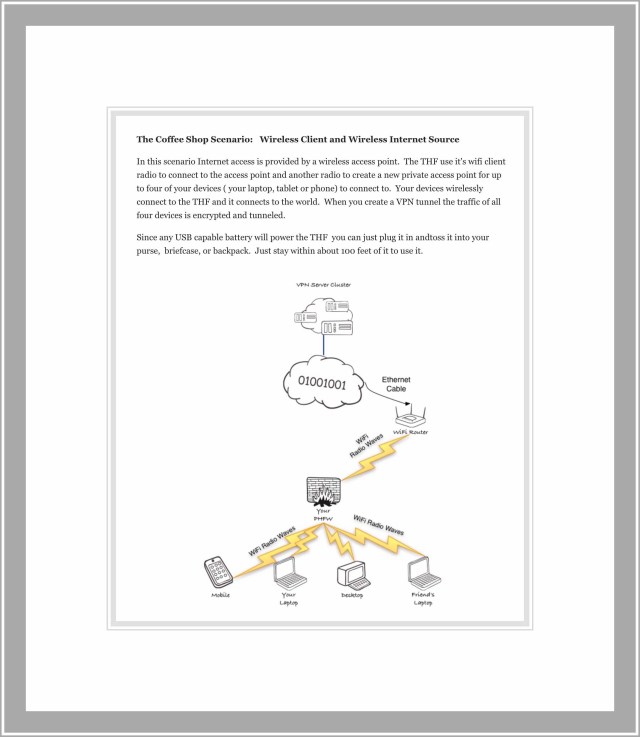
Example of how my Tiny Firewall protects me
How Does a Portable Firewall with a VPN Protect You?
The way you use a portable Firewall is by connecting it to a network and then connecting your devices to it. Because it stands between you and any dangers it can protect you in numerous ways which depend upon your preferences. It can offer security services which examine all of the incoming and outgoing traffic to decide if it’s safe or not before allowing it. It can include ad blockers and malware blockers. Last, with the addition of a VPN, it can keep all of your data hidden so no one has access to it.
Think of the VPN part like this. The Firewall connects to the public network then it uses the VPN to create a protected tunnel for all your communications to go through. So even though your data is traveling on a public network…it’s doing so inside this protected tunnel. No one can see it or access it. Your data is completely hidden.
Why is a Portable Firewall the Best Solution?
The main reasons boil down to speed and cost. When you use a cellular hotspot you’re using cellular network speeds…when you’re using a firewall you’re using true network speeds like those that are provided by broadband, DSL or Fiber. Cellular plans are expensive too and recurring. You never know in advance how expensive though because you can go over your plan’s limits easily and end up incurring huge charges for that. I know this from personal experience too.
A few years ago we arrived home from a Mediterranean cruise to a $13,000 cell phone bill!
During our cruise I had been in constant contact with our cell provider to make sure that we weren’t incurring large, unknown costs. I spent (really wasted) so much time doing that…because it took hours sometimes to even reach someone at our cell provider’s international division. But my actions were our saving grace too. Had I not done that our cell provider would not have ultimately reversed all those charges.
Aren’t VPN’s Expensive?
There is an ongoing cost for using a VPN but it’s pretty reasonable when compared to a cell plan. Our Tiny Firewall’s chosen VPN costs about $100 a year. Because I can have up to 4 users on my Tiny Firewall at the same time, it’s like I’m getting 4 VPN subscriptions for the price of one. That’s equivalent to 2 months of the cost for our Verizon Hotspot’s service…which is the lowest priced plan Verizon offers.
Are VPN’s Slow and Hard to Use?
That’s what I always thought. But I guess things have changed a lot. I think a VPN’s speed is actually determined in great part by the speed and bandwidth of the network you’re using. So our network at home gives us 300 Mbps down and when I tested out the new VPN on it we ran two iPads simultaneously streaming YouTube videos. The speed was amazing! There was no buffering and the display quality was excellent!
Using the VPN inside our Tiny Firewall is super easy too. We just turn it on with a little slider button.

Tiny Hardware Firewall’s website
My Review of the Tiny Hardware Firewall
Using the VPN was super easy…but setting up the Tiny Firewall initially wasn’t. Luckily I had help in the form of the network consultant who was installing our new home Firewall.
I’m super lucky that I had his help, because I learned a lot about how these work and what’s involved in the setup. Now that I understand the process, I know I could do it…but I would have struggled before.
It took about an hour for he and I working together to get it all set up. Then after he left I played around with it for about a half hour to make sure I knew how to use it. I wrote a Step by Step guide for myself to remember how to use it, which I thought I would share here.
I probably could have setup the Tiny Firewall myself…but it probably would have taken me much longer to do. Maybe around 4 or 5 hours total. I did end up having to go through about half the setup again the first time we traveled using it, because no one but me could join the network it broadcast. In my efforts to discover the cause of the problem, I reset much of what our firewall guy had accomplished. So in the end I had to learn almost everything about the setup process myself too. The Tiny Firewall’s 27 page User Guide was my only resource and it assumes a lot of networking expertise I lack. But the guide is comprehensive and after rereading it multiple times I finally understood enough to get ours functional again.
Using the Tiny Firewall is Easy & Seamless Once it’s Setup
So here’s my primary review:
The Tiny Hardware Firewall is simple to use and amazing once it’s setup. When you want to use it somewhere you first join the firewall’s network with your device, and then use a browser to have the firewall join the public network you’re near. While doing that step you also enable the VPN. The whole process takes less than a minute.
It’s well worth the price of $132 that I paid for it. Part of that price is the $91 for the VPN which we’ll need to renew in 1 year’s time. The VPN which is HotSpotVPN is excellent and there is a support link for that if you run into trouble. WiFi Consulting, the company that makes the Tiny Hardware Firewall (THF) also owns and operates this VPN too. Which probably explains why the 2 work so seamlessly together.
The Firewall itself is also excellent…it’s got so many great features and it does some really cool things. That’s why I think the setup was hard, because despite the User Guide being excellent and long…27 pages…it’s probably a little too long for the average user to sit down and read in it’s entirety. Especially because it’s pretty dry reading and it uses a lot of network terminology that most people don’t understand.
You can’t fault a product for being too excellent!
For example, the Firewall operates in 3 main modes…Client Mode, Access Point Mode and Wireless to Wireless Mode. There are descriptions of what these are and even diagrams, but for people who’ve never done much networking, even those things aren’t really enough. Everything about the Tiny Firewall is based upon those 3 modes, so understanding them and which one is most appropriate for your own use is critical.
My understanding of what the 3 modes are.
Client Mode
Client Mode is a wireless connection between two routers only. A router in Client Mode connects to another wireless Access Point (the host router). It uses its wireless connection as the WAN interface (or maybe it’s the WLAN interface…I always get those confused) and shares the internet connection only to the LAN ports. It’s used in networking a lot as a bridge, but for the Tiny Firewall’s purpose, this mode is primarily used for the initial setup.
Access Point Mode
AP mode is most often used to turn a wired connection into wireless one. The Tiny Firewall has 2 Ethernet ports…one for LAN and one for WAN. If you’re in a setting like a hotel where only wired internet is provided, you can use AP mode to create your own wireless network.
Wireless to Wireless Mode
This is the mode we primarily operate the Firewall in. It means that our Firewall device connects to a public network wirelessly and then we in turn connect to the Firewall wirelessly with our mobile devices.
My Suggestion to Tiny Hardware Firewall’s Developer
Personally, I think the developer should create a YouTube video that explains the setup process. It doesn’t need to be fancy or long, but it should show the screens involved and explain how and why average users would use the various features.
How to Use the Tiny Hardware Firewall
This is how I used the Tiny Firewall my first time on a recent family vacation. Once the Firewall was all setup, we used it in Wireless to Wireless mode. Which meant I connected the Firewall to a hotel’s wireless network, turned on the VPN and then had it broadcast a new network for my family to join.
The Steps We Follow Each Time We Want to Use the Firewall
Me Only – First login to the router to enable the VPN:
- Give the router power by plugging it in.
- Wait about 3 minutes for it to boot up.
- Join the wireless network it creates. (I gave this wireless network a randomly generated ssid and password during the setup process.)
- Go to the IP address for it using a web browser.
- Connect it to the hotel’s WiFi
- Turn on the VPN
How Other People Get On to The VPN & Firewalled Network
- Go to network settings on your device and look for the wireless network the Tiny Firewall broadcasts.
- Join the network by entering the password (so far all the passwords I’ve seen it generate are in all caps)
- On ios devices turn off ‘Ask to Join Networks‘ so your device stays on the protected network.

The TOR Browser uses an onion for a logo
Some More Cool Features of the Tiny Firewall | The TOR Network
My model allows up to 4 devices on the network at the same time. There are 2 smaller versions which I believe are single user. With mine, internet connections can be hardwired using an Ethernet connection or wirelessly. There’s also a TOR network included which I’ve never tried but have always wanted to explore. TOR is the way hackers get onto the deep web…it’s a highly protective browser that keeps you extra safe and hidden and virtually untraceable. You can read more about TOR here and visiting the dark web here. From what I’ve read recently though the dark web isn’t really around much anymore, since Silk Road an infamous market for criminals was taken down about 3 years ago.
In October 2014 a popular Wired Magazine writer, Andy Greenberg, wrote about a device very similar to the Tiny Firewall in what turned out to be one of the most read articles of the month at Pocket, a widely used Read it Later service. His article, ‘With This Tiny Box, You Can Anonymize Everything You Do Online‘ talked about a new Kickstarter campaign for a similar type of device by anonabox which was developed and refined for the sole purpose of running the open source software Tor, considered the best and most secure way to access the Internet anonymously. All traffic coming out of or going into your computer or network is encrypted this way. The result is strong, secure anonymity. Using the anonabox hides your location, as well as all the other personal data that leaks through ordinary Internet use. In the end the anonabox device had a lot of problems and didn’t end up becoming the panacea everybody had hoped for. There are several other brands of similar devices now that offer various features, but all are intended just for TOR access primarily. So, while many people including me believed TOR is used only by criminals, it’s actually used by regular people too who just want anonymity online.
The Wired article states that “no tool in existence protects your anonymity on the Web better than the software Tor, which encrypts Internet traffic and bounces it through random computers around the world. But for guarding anything other than Web browsing, Tor has required a mixture of finicky technical setup and software tweaks. Now routing all your traffic through Tor may be as simple as putting a portable hardware condom on your ethernet cable.” At that time he described similar efforts to develop devices of that nature with varying degrees of success, all priced similarly to that of the Tiny Hardware Firewall’s price of around $40 for the base unit without the VPN service.
Now, 2 years later with the addition of the TOR network as a feature bundled along with a fast, reasonably priced VPN, the Tiny Hardware Firewall appeared to me to be the one standout amongst tech-minded individuals, which is why I chose it. There might be easier solutions…but I wanted the best and I was willing to put in the time learning to have it.
Where to buy the Tiny Hardware Firewall
I purchased mine from the developer’s website. I got the most expensive version which allows 4 users both wired and wireless…and mine has an antenna. We discovered setting it up that the antenna really does make a difference too. Mine was about $132 including shipping. That price also includes a one years subscription to their VPN service. There are smaller, less expensive models too…there are four in total. Ours arrived in about 3 days via UPS and we had to sign for the delivery.
Here’s a link to the website where I purchased ours from.

4 models of the Tiny Hardware Firewall
2 Great ‘Must See’ Tools if You Want to Quickly Learn How Easily Public Networks are Hacked & How to Stay Safe
If you don’t have a lot of time to spend learning about ways to stay safe, this section includes 2 links which together should bring you up to speed on everything you need to know to understand the threats and to keep yourself safe. So, consider these links together as a mini course about public WiFi safety.
This excellent 20 minute YouTube video demonstrates an easy method hacker’s use to hack public networks with a device similar to my new Tiny Firewall (which is basically a tiny router.) At about 17 minutes in he shows how to use a device like the Tiny Firewall for good to protect yourself.
This great article written by the FTC adds some more information you should know about for keeping safe.
Additional Resources
Here’s a great YouTube video that tells you a lot more about the Tiny Firewall
Here’s a link to the Tiny Firewall’s User Guide
A link about how to find out what kind of encryption a WiFi is using
WiFi Consulting offers another portable firewall called the BlackHoleCloud. When I got mine I was familiar with this but I didn’t entirely understand the differences. Since I had more information at my disposal on the Tiny Hardware Firewall, that’s the one I went with. But now I recognize that this might be an even better, faster solution so I’m including a link to a great review about the BlackHoleCloud Firewall.
Make Sure Your Home Network is Secure Too
Even when you’re not traveling you could be exposed to hackers if you haven’t bothered to secure the network that you use everyday. It’s not difficult to secure your network and it can be done in less than half an hour all by yourself. Nothing additional is needed other than you’re taking a little time to learn about why it’s important and how to do it. I wrote this guide for securing your home network, after I realized that somehow ours had become unsecured. Which tells me that this is something I need to check once in a while just to make sure my security is still in place.
If you’re wondering why securing your home router is so important, you can read my article about why I write this blog and how I became an unwilling participant to the world of cyber security initially when our home network was taken over by a Botnet.
My Family’s Awful Experience Invaded by a Botnet Led to the Creation of vsatips

Comments
Please leave a comment if you feel inspired! I’d especially love to hear about other solutions you may have tried.
Form
contact-formcontact-field label=’Name or Nickname if you don%26#039;t want your real name’ type=’name’ required=’1’/contact-field label=’Comment’ type=’textarea’ required=’1’//contact-form
